Introduction
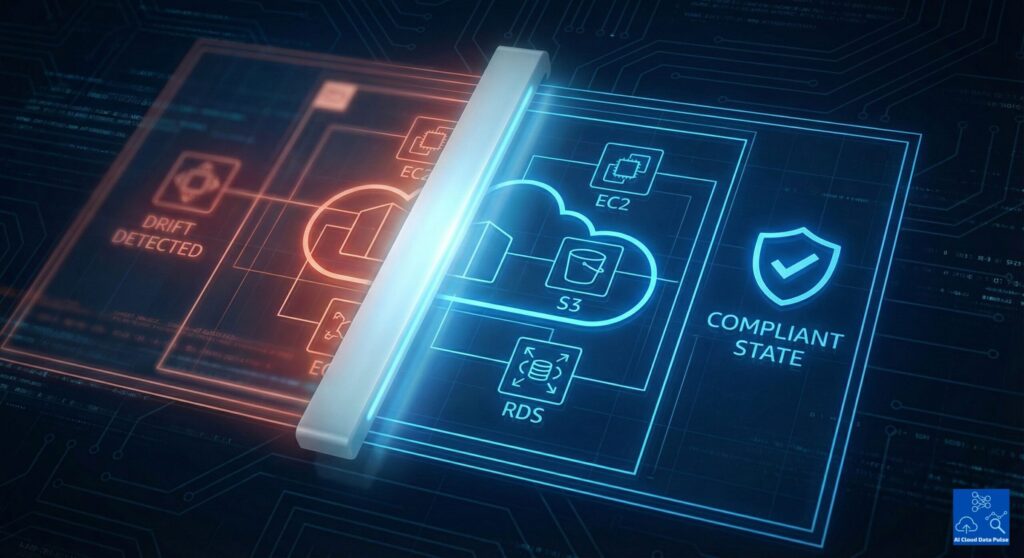
AWS environment compliance is a core requirement for any security posture and is enforced through AWS Config rules monitoring. This service complements logs and metrics that only explain what happened, but not whether environments are compliant. However, security teams need visibility into configuration state and not simply events to evaluate an environment’s security posture. In this case, compliance failures generally stem from drift over time and not from single events. It follows that governance needs continuous evaluation and not point-in-time checks.
AWS Config performs this by tracking resource configuration over time by applying a set of rules for monitoring compliance. These rules act as automated compliance checks against expected baselines to measure drift. This continuous evaluation enables near-real-time visibility into non-compliant resources and continuous security posture evaluation. AWS Config also provides an auditable history to support governance, along with remediation workflows and integrations.
For a broader view of how AWS Config fits within AWS observability and security telemetry, see the AWS Logging and Monitoring Guide.
What AWS Config is
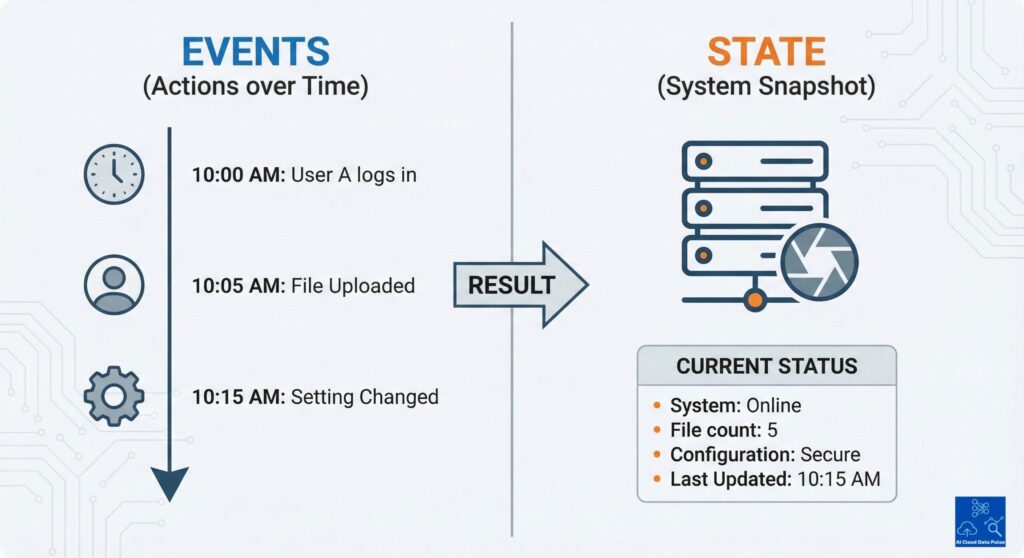
AWS Config is a configuration-tracking and monitoring service, not an event log; it applies rule sets to resources to determine their compliance. This provides teams and automated processes with continuous visibility into resource configuration changes over time. It also provides a central view of the current state across accounts and historical configuration snapshots. Accordingly, the focus is on how resources are configured, not on how they are utilized.
In contrast to logging and monitoring services, AWS Config tracks whether configurations remain correct and comply with its rules. This is different from event-driven logs that capture what happened or metrics on the current system state. Hence, metrics and logs provide behavioral insight and not compliance guarantees. Meanwhile, an environment can experience configuration drift between logged events and normal operations. AWS Config addresses this gap by verifying the state of resources against expected baselines.
Compliance is an essential aspect of auditing, and configuration state serves as an auditable source of truth for compliance reviews. Therefore, AWS Config supports multi-account and organizational governance through compliance monitoring with its rules set. This enables the identification and tracking of non-compliant resources over time. Furthermore, this serves as the foundation for automated remediation and continuous assurance through services like AWS Systems Manager, EventBridge, and Lambda functions.
How AWS Config Rules Enable Compliance Monitoring
Config rules are declarative definitions that monitor compliance with AWS resources and are not procedural logic. They evaluate resource configurations against expected baselines, and the rules’ logic implicitly defines these expected configuration baselines. Once these rules are evaluated for a resource, resource compliance is expressed as either compliant or non-compliant. Having AWS Config apply these rules ensures consistency across accounts and regions, which is difficult to achieve manually. These rules enforce security, operational, and governance standards for all AWS resources. Having AWS Config rules define compliance separates what compliance looks like from how it is implemented. The latter is typically handled by downstream automation workflows.
Config rules continuously monitor AWS resource configuration compliance and replace manual or periodic reviews. These are change-triggered assessments that respond to configuration updates, similar to the continuous integration mindset. However, AWS Config does apply periodic evaluations to detect any resource configuration drift occurring without any recent change events. Significantly, compliance checks occur during normal operations so as to address any arising non-compliance issues and not during audits. This provides security teams and downstream automated processes near-real-time visibility into any configuration deviations. AWS Config focuses solely on detecting resource configuration drift regardless of application behavior or resource usage.
Additionally, AWS Config rules move from point-in-time audits to continuous compliance posturing by continually monitoring resource configurations. This reduces manual reviews and checklist-driven assessments, which are snapshots, in favor of Config, which provides near-real-time visibility. By reducing manual reviews, there are clearer and consistent compliance signals across environments. Subsequently, there is early detection of non-compliance and resolution of resource configurations prior to any audits. Furthermore, compliance status feeds into reporting, alerting, and assurance processes. This helps form the foundation for scalable governance without the operational overhead involved with manual processes.
Managed vs Custom AWS Config Rules
Managed AWS Config Rules
AWS provides a predefined set of Config rules that reflect common security, compliance, and monitoring expectations. These are opinionated baselines that align with widely accepted best practices in the industry, acquired through experience. They are out-of-the-box and ready-to-use, with no need for custom rule development, so teams can apply them immediately.
Managed AWS Config rules are typically suitable for baseline compliance and foundational security controls, usually at the root organization or account. They are also effective for early-stage or standardized governance programs for organizations commencing their AWS journey. Additionally, they provide organizations with consistent enforcement across accounts with minimal operational overhead.
Custom AWS Config Rules
However, organizational compliance and monitoring logic are often beyond the scope of predefined AWS Config rules and AWS-managed baselines. There are internal standards and contextual policies that organizations need to encode into AWS Config rules. Also, organizations need the flexibility to evaluate environment-specific or conditional requirements that are outside the scope of AWS-managed baselines.
There are other scenarios where organizations need to establish custom AWS Config rules for compliance monitoring. A typical scenario is where regulatory or internal requirements are not covered by baseline rules. Another is where compliance conditions depend on tags, environments, or organizational context. Also, more mature governance programs often require bespoke policy definitions.
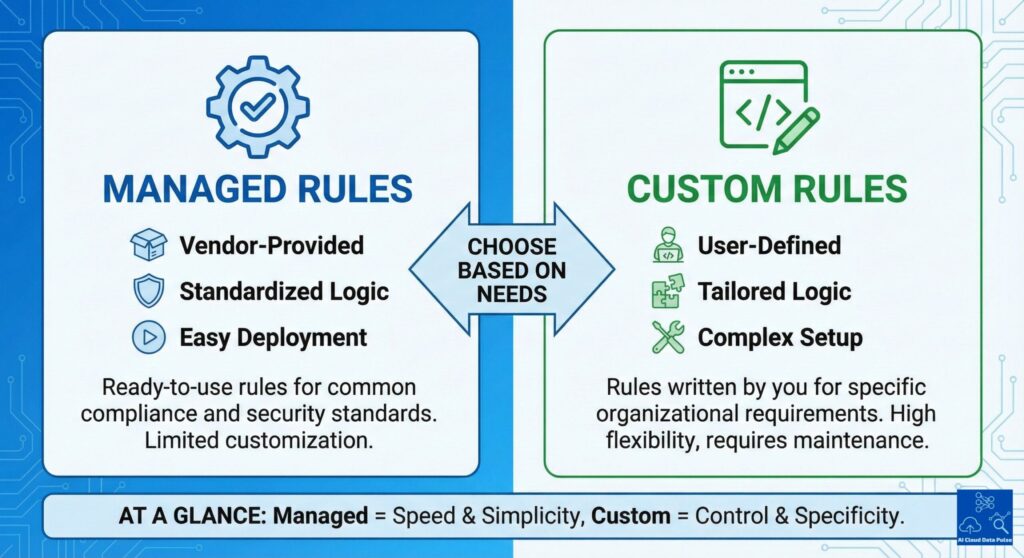
Typical trade-off between managed and custom rules is increased flexibility with custom rules at the cost of higher implementation and maintenance effort. However, custom rules provide greater ownership and accountability for policy definition and lifecycle management.
Governance and Continuous Compliance with AWS Config Rules
AWS Config enables automated governance that is defined as maintaining a compliant configuration over time. Organizations traditionally performed governance through regular audit checks, where AWS now shifts this to ongoing oversight. Therefore, AWS Config rules provide persistent compliance signaling with ongoing monitoring, where downstream systems can remediate automatically. Security and platform teams can treat the compliance state of AWS resources as the foundation of governance, reflecting organizational policies. Continual monitoring by AWS Config embeds compliance into operations, and it is no longer treated as an exception. Here, it focuses governance on preventing drift and not just simply reporting violations.
AWS Config also enables governance and compliance at scale by applying uniform rule enforcement by monitoring across accounts and regions. This ensures a consistent compliance evaluation that is independent of the team or workload, where audit teams would have varying results. It also enables early detection of non-compliant configurations before audit windows, allowing for timely remediation. Additionally, this reduces the need for manual review cycles and reporting overheads, resulting in cost savings for an organization. An added benefit is that it provides continuous posture visibility for security and platform teams, allowing them to make more informed decisions. By reducing manual review cycles, organizations benefit from scalable governance without the proportional increases in operational effort.
Real-time monitoring by AWS Config rules provides security and platform teams with clear ownership and accountability for the compliance state. They also benefit from having improved audit readiness without the need for audit-driven behavior and last-minute panic. Significantly, AWS Config enables integrating compliance into day-to-day operations by applying the concepts behind continuous integration and delivery. It also provides the early identification of misconfigurations, thereby reducing risk instead of discovering them during an audit. This establishes the foundation for mature security and risk management practices.
Integrating AWS Config with Security and Monitoring Workflows
Centralized Visibility with Security Hub
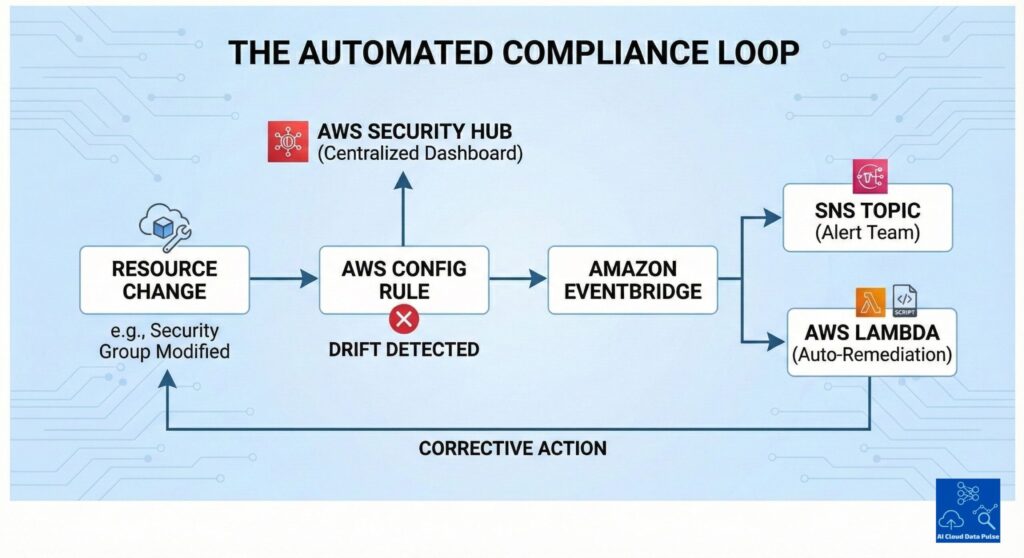
Integration with Security Hub frames AWS Config rules that emit compliance findings as standardized signals for downstream monitoring. Subsequently, Security Hub serves as a central aggregation layer for both compliance and security data across both regions and accounts. Security Hub also normalizes AWS Config findings alongside other security controls for correlation, enabling further investigation. This centralized view is especially useful when correlating AWS Config compliance findings with threat detection signals, such as those generated by Amazon GuardDuty, to provide a broader security context. This provides unified visibility across accounts, regions, and services, enabling teams and automated processes to make better-informed decisions. Additionally, there is a clear separation between compliance detection provided by AWS Config and centralized visibility provided by Security Hub.
Notifications and Event-Driven Response with SNS and Eventing
Unlike audit reports that are static, AWS Config ensures that compliance state changes generate events that security teams can monitor. Converting these events into notifications using SNS allows for timely awareness without the need for teams to perform constant dashboard monitoring. Significantly, this enables automated responses and escalations to any configuration changes via EventBridge using event-driven triggers. These separate services enable decoupling of detection from notification and response logic, allowing for more flexible architectures. Additionally, this allows flexible routing of compliance signals to security teams, systems, or workflows, providing comprehensive management of resource compliance.
Multi-Account Governance and Organizational Oversight
Utilizing native AWS services enables consistent application of Config rules across multiple accounts and regions for compliance monitoring. Integration with Security Hub centralizes the aggregation of compliance state at the organizational level, allowing central oversight by compliance teams. This reduces the need for account-by-account compliance reviews, which were often performed manually, resulting in errors and inconsistencies. Additionally, this provides clear oversight for platform and security teams without the need for local enforcement, simplifying their operations. This scalable governance model aligns with AWS Organizations structures, allowing implementation of AWS best practices.
Limitations and Cost Considerations of AWS Config
Operational and Technical Limitations
AWS Config rules, while highly powerful, do not provide insight into runtime behavior when evaluating and monitoring configuration state compliance. Neither do they provide any visibility into application logic or workload usage correctness, which is provided by other services. Compliance signals primarily indicate baseline alignment but do not provide any security guarantees. Therefore, there is a risk of false confidence when used without any complementary controls.
Also, AWS Config has near-real-time latency, but it is not instantaneous, which is often more appropriate for governance activities. Additionally, teams relying on change events may miss configuration drift that does not produce a detectable change event. Therefore, they need periodic evaluations to detect certain types of configuration drift. The other challenge is increasing noise and operational cognitive load when teams allow rules to sprawl. Hence, teams should practice deliberate rule scoping to maintain signal quality.
Cost Considerations and Scaling Impacts
AWS Config rules applied to compliance monitoring also incur associated costs for configuration items, rule evaluations, and snapshots. Platform teams can experience cost growth driven by account count and resource churn due to increased monitoring by AWS Config. This is further amplified within large or highly dynamic environments.
Platform teams must manage AWS Config rules by selectively enabling rules based on risk and compliance priorities. Instead of exhaustive monitoring that drives up costs, they should align compliance coverage with governance objectives that support best practices. As with any other cloud activities, cost awareness must form part of sustainable compliance operations.
Closing Synthesis
Platform teams must always remember that AWS Config is positioned for state-based governance and not as a logging service. Significantly, AWS Config reframes compliance as continuous assurance instead of audit preparation. Hence, AWS Config rules for compliance monitoring translate governance intent into enforceable signals. Subsequently, compliance state services act as the authoritative compliance reference with Config rules expressing this compliance state. The most important outcome is that continuous visibility provided by AWS Config enables proactive governance rather than reactive governance.
Platform teams must recognize that AWS Config only truly delivers value in maintaining security posture when it is combined with complementary security signals. They should always practice thoughtful rule selection that is aligned with risk and governance priorities. This is driven by the idea that governance effectiveness is driven by signal quality over rule quantity. Additionally, there is a mind shift to treating continuous compliance as an operating model rather than compliance evaluation only during audits. Accordingly, architectural best practices have positioned AWS Config as one of the pillars for broader security and risk posture.
Further Reading and References
AWS Official Documentation – AWS Config
AWS Certified Security – Specialty (SCS-C02) Exam Guide by Stuart Scott
Multi-Cloud Architecture and Governance by Jeroen Mulder
AWS: Security Best Practices on AWS by Albert Anthony
Practical Cloud Security: A Guide for Secure Design and Deployment by Chris Dotson
Security Engineering: A Guide to Building Dependable Distributed Systems by Ross Anderson
Affiliate Disclosure: As an Amazon Associate, I earn from qualifying purchases. This means that if you click on one of the Amazon links and make a purchase, I may receive a small commission at no additional cost to you. This helps support the site and allows me to continue creating valuable content.