Introduction – Why AWS Config Rule Evaluation Modes Matter
AWS Config uses defined compliance rules to evaluate recorded configurations for supported AWS resources, with evaluation modes that represent different compliance checks. It builds a historical timeline of resource states, and the compliance status results from a configuration evaluation at a given point in time. Compliance status also reflects configuration state over time, not a single snapshot.
Evaluation modes exist because different rules require different evaluation timing based on configuration change frequency. Therefore, evaluation modes define when AWS Config assesses recorded configurations for compliance.
Subsequently, applying incorrect evaluation mode assumptions can potentially create gaps in compliance visibility. This results in blind spots where platform operations can miss critical information, compromising security posture.
How AWS Config Evaluates Rules
AWS Config monitors resource configuration by recording configuration changes for all supported AWS resources. Accordingly, each recorded configuration item represents a resource state at a point in time for evaluation. AWS Config does not evaluate live resources, but applies rule evaluations on recorded items to determine configuration drift for each resource.
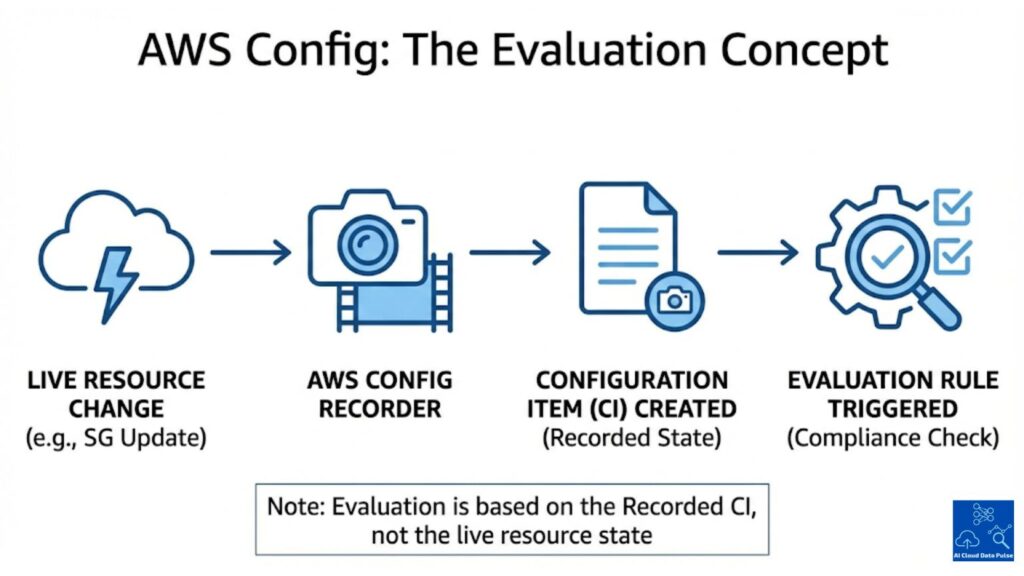
However, AWS Config evaluates the configuration conformance of resources by applying rule logic to each recorded configuration item. There are two main categories of AWS Config rules: AWS-managed and custom Lambda-backed. Organizations author custom rules to align with their policies. Therefore, applying the evaluation rules determines whether a configuration item meets compliance criteria established by either AWS or the organization.
Subsequently, the evaluation results assign a compliance status to each resource for monitoring. This compliance status can transition between COMPLIANT and NON_COMPLIANT depending on the outcome of evaluation rules. Accordingly, AWS Config maintains status history for each configuration item over time for monitoring.
These evaluations are driven by AWS-managed and custom rules, which are commonly used for broader AWS Config compliance monitoring and governance.
Continuous Evaluation Mode
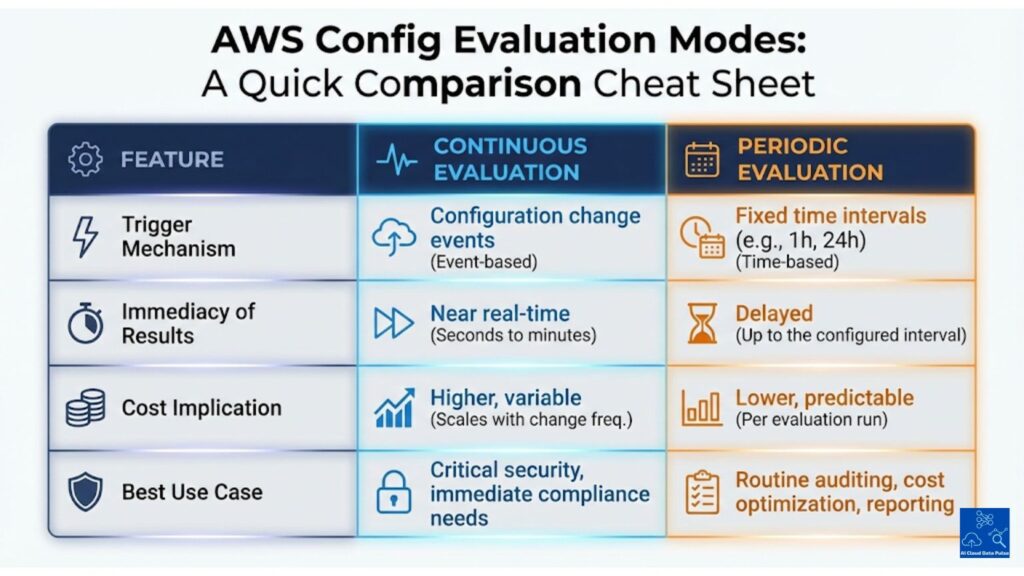
AWS Config performs continuous evaluation by triggering rule evaluations whenever it records configuration changes. This ensures that evaluations occur automatically without scheduled intervals. Hence, it supports near-real-time compliance assessments after configuration changes, enabling timely monitoring of configuration compliance. However, this continuous evaluation only applies to supported rules and resource types, otherwise AWS Config reverts to periodic evaluation.
To achieve continuous evaluation, AWS Config listens for change notifications whenever supported resource types are created, modified, or destroyed. When it detects a change, it captures the updated resource metadata and records this by storing a configuration item representing the resource’s state. Once it has created and stored the configuration item, it triggers evaluation for that item. This ensures that rule evaluation occurs without waiting for a scheduled interval.
Continuous evaluation has several significant benefits, where personnel and automated response systems detect compliance drift shortly after configuration changes occur. Therefore, they can identify any non-compliant resources with minimal delay. This also provides security and governance teams with near-real-time visibility of AWS compliance. Furthermore, this facilitates a more rapid response and remediation whenever resources become non-compliant.
However, continuous evaluation is only available for supported rules and resource types and is not generally available. For non-supported rules and resource types, AWS needs to employ either scheduled or aggregated evaluation of resource compliance. Accordingly, it must align evaluation mode selection with rule capabilities and resource support.
Periodic Evaluation Mode
While continuous evaluation is event-driven, periodic evaluation runs rule evaluations on a defined schedule. These are time-based and not triggered by changes in the configuration, and run independently of configuration change events. AWS Config runs compliance checks at regular intervals, where it applies either system or customer rules to determine if resources are compliant.
Periodic evaluation rule configuration defines the timing mechanisms, including the evaluation frequency of applying configuration rules to resources. Hence, these evaluations run at scheduled intervals in contrast to continuous evaluations that run whenever a change event occurs. Subsequently, periodic evaluation uses only the latest recorded configuration items for evaluation, even if there are preceding configuration items since the last evaluation. Hence, individual configuration changes do not immediately trigger evaluation.
System designers will choose periodic evaluation since compliance is assessed on a predictable and consistent schedule. Often, this is suitable for broad or organization-wide compliance checks where continuous evaluation becomes too costly and resource-intensive. Since it decouples evaluation from change events then evaluation frequency is lower for resources with frequently changing configurations. Accordingly, periodic evaluation helps balance compliance monitoring with operational cost considerations.
Whereas periodic evaluations’ main advantage is cost, compliance drift in resources may persist until the next scheduled evaluation. This especially makes periodic evaluation unsuitable for detecting rapid or high-risk configuration changes. Therefore, there is a trade-off between immediacy and predictable evaluation cadence.
Continuous vs Periodic Evaluation: Key Differences
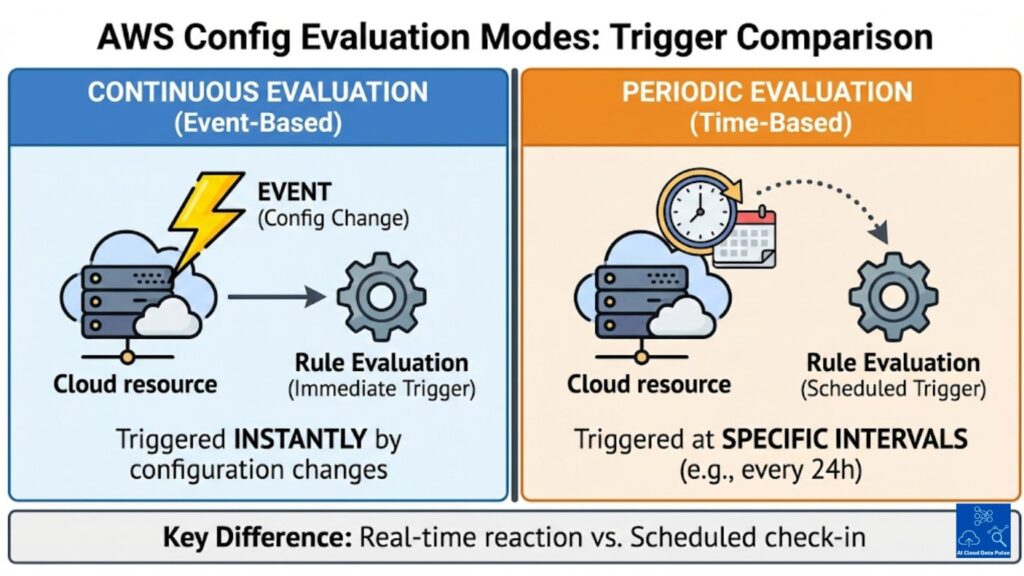
AWS Config continuous evaluation is triggered by configuration change events, where each configuration item invokes the evaluations for compliance. Conversely, periodic evaluation runs are based on a defined schedule in which evaluations occur at regular intervals. Hence, continuous evaluation is near real-time, whereas periodic evaluation is delayed by the evaluation interval.
The core advantage of continuous evaluation is that it minimizes the window of undetected non-compliance of resources. However, selecting periodic evaluation introduces a delay between resource configuration drift and its detection. Accordingly, the risk exposure depends on the selected evaluation timing rather than the rule logic.
However, continuous evaluation increases evaluation frequency for frequently changing resources, which can quickly drive up costs. In comparison, periodic evaluation puts a cap on evaluation executions through scheduled triggering, keeping costs steady. Therefore, costs and scaling behavior have different profiles based on configuration change frequency and evaluation mode selection.
Therefore, continuous evaluation prioritizes immediacy and rapid risk detection, with cost control potentially spiralling out of control. Whereas periodic evaluation prioritizes predictability and broad governance coverage, since costs are known in advance.
Choosing the Right Evaluation Mode
There are several considerations when selecting the AWS Config compliance rules evaluation mode. Engineers should identify high-risk resources since they require quicker detection of non-compliance. Consequently, if they have delayed compliance visibility, then that increases the exposure to security incidents. Therefore, evaluation mode selection should reflect the acceptable risk window.
Engineers should also be mindful that frequently changing resources increases the AWS Config compliance evaluation frequency when selecting continuous evaluation. Also, selecting scheduled evaluation provides predictable costs in high-churn environments, and cost is always a principal driver. Therefore, engineers must make a trade-off between immediacy and operational cost when selecting the evaluation mode.
The core principle is that evaluation modes are not selected globally but on a rule-by-rule basis, depending on the resources monitored. Accordingly, most environments establish a mix of continuous and periodic evaluations. Henceforth, governance selects the evaluation mode that aligns with compliance goals while accounting for operational constraints.
AWS Config Rule Evaluation Modes: Key Takeaways
Specifically, AWS Config evaluates compliance based on recorded configuration items rather than live resource states. Significantly, evaluation modes specify when compliance is assessed, thereby shaping risk exposure and cost behavior. Security teams should therefore select either continuous or periodic evaluation on a per-rule basis to balance immediacy and governance.
These evaluation results typically flow into centralized logging and monitoring pipelines, as outlined in our AWS logging and monitoring guide.
Further Reading
AWS Certified Solutions Architect Study Guide by Ben Piper and David Clinton
Affiliate Disclosure: As an Amazon Associate, I earn from qualifying purchases. This means that if you click on one of the Amazon links and make a purchase, I may receive a small commission at no additional cost to you. This helps support the site and allows me to continue creating valuable content.