Introduction: Custom AWS Config Rules Best Practices
The AWS Config service simplifies compliance enforcement for AWS resources in an intuitive, integrated manner. Platform teams can adapt AWS Config to organizational policies using custom AWS Config rules, provided they follow best practices. Following best practices is key because rule creation is easier than long-term ownership, leading to a proliferation of rules. Significantly, the proliferation leads to a degradation of the compliance signal.
The current literature focuses on writing AWS Config rules, with minimal emphasis on best practices. There is scant discussion on rule lifecycle ownership, unlike other cloud resources. This is a result of underestimating the required maintenance and the blast radius. The other mistaken belief is that increasing operational cost will automatically lead to security gains. For a broader discussion of how AWS Config rules support compliance monitoring and governance at scale, see the foundational overview.
This article provides only a decision framework for best practices, with no intention to serve as an implementation guide. It explores the guardrails for responsible custom rule design and adherence to signal quality prioritized over rule volume. It is worth regarding each custom AWS config rule as a small production system.
Managed vs Custom: Decision Lens
AWS Config rules nominally reflect organizational governance and policies, and platform teams should not regard them as features in the normal sense. It follows that defaults matter more than flexibility since stable platforms are a key governance objective. Accordingly, managed rules serve as the compliance baseline for pursuing this objective. However, since organization policies vary, they require custom AWS Config rules as explicit exceptions, provided they follow best practices.
A core custom config rule best practice is to use managed rules as the default, since they are AWS-maintained and provide default logic. Another core reason for leveraging managed rules is that they receive automatic updates and improvements. An additional benefit is that managed rules have predictable scope and behavior, thereby minimizing ambiguity, cognitive load, and unintended side effects. This also leads to lower maintenance and ownership costs, since these are borne by AWS, and reduces the blast radius.
Understanding custom AWS config rules leads to an appreciation of best practices since they involve Lambda execution and runtime lifecycle maintenance. They also add to the burden of code ownership and the knowledge decay that comes with it. Significantly, the custom rule code base may drift from its original intent, adding another factor to monitor alongside configuration drift. These all contribute to expanded failure and blast radius, necessitating ongoing testing and change management.
Therefore, a core custom AWS config rule best practice is to exercise discretion when applying them. Primarily, it is the ability to discern when policy requirements are not covered by managed rules. Another criteria when to use custom rules is when compliance logic is stable and unlikely to change. Also, it is essential that governance assigns clear ownership and maintenance responsibility for all custom rules. Ultimately, use custom rules when their signals exceed operational and blast radius costs.
Best Practices: Patterns That Justify Custom AWS Config Rules
Following established patterns to justify custom AWS Config rules will prevent ad-hoc rule creation. Hence, a central best practice is to use patterns to justify AWS Config rules before implementing them. Using repeatability to enforce this restraint will ensure that custom rules are not created when AWS-managed rules suffice.
Pattern 1 — Policy Logic Beyond Resource Configuration
The unique characteristic of AWS Config rules is that they directly implement governance policy. Policies that depend on multiple configuration attributes may require custom AWS Config rules. Additionally, whenever resource relationships influence the desired compliance state, there is scope for customization. Moreover, when policies need context beyond declarative checks, then customization is necessary. In each of these scenarios, managed rules lack the necessary expressiveness to implement these policies, necessitating custom config rules.
Pattern 2 — Cross-Resource or Cross-Service Validation
Cross-resource or cross-service validation scenarios likely require custom AWS Config rules when spanning multiple AWS services. In these scenarios, compliance depends on the correlated state, making policies more complex than standalone resources. Furthermore, policies infer correctness from usage context, which extends beyond managed rules, necessitating the creation of custom rules. Additionally, managed rules avoid cross-service coupling, and policies that require this certainly need custom AWS Config rules, making this a best practice.
Pattern 3 — Stable, Regulation-Driven Requirements
Many scenarios have regulatory or contractual mandates that managed AWS Config rules do not support. When these compliance definitions are clear and unambiguous, it is fitting to implement them through custom AWS Config rules. Additionally, when these policies are not frequently changed, this reduces the burden of custom rule maintenance. Also, custom AWS config rules are appropriate when there is long-term policy ownership, and maintenance is expected.
Pattern 4 — Explicit Risk Acceptance with Defined Ownership
Best practices recommend using custom AWS Config rules to mitigate known, documented risks not supported by managed rules. They also recommend formally assigning ownership and maintenance to these rules for traceability. Additionally, they recommend establishing retirement criteria upfront, defining full lifecycle management for custom AWS Config rules.
Custom AWS Config Rules Best Practices: Maintenance, Blast Radius, and Ownership
Best practices need to properly manage the maintenance, blast radius, and ownership of custom AWS Config rules.
Maintenance as an Ongoing Operational Cost
Because engineers must implement custom AWS Config rules as Lambda functions, they inherently take on Lambda runtime and SDK lifecycle management. Since rules are expressions of policy, custom rules may experience dependency drift when library updates subtly alter their behavior. Hence, they drift from expressing the policy that they originally expressed. Other AWS environment changes can affect the execution of custom rules even though the compliance logic is unchanged, necessitating retesting. These inherent maintenance costs accumulate over time due to continual changes in the libraries they depend on and AWS environmental changes. These costs include code updates and associated validation.
Blast Radius of Custom AWS Config Rules at Scale
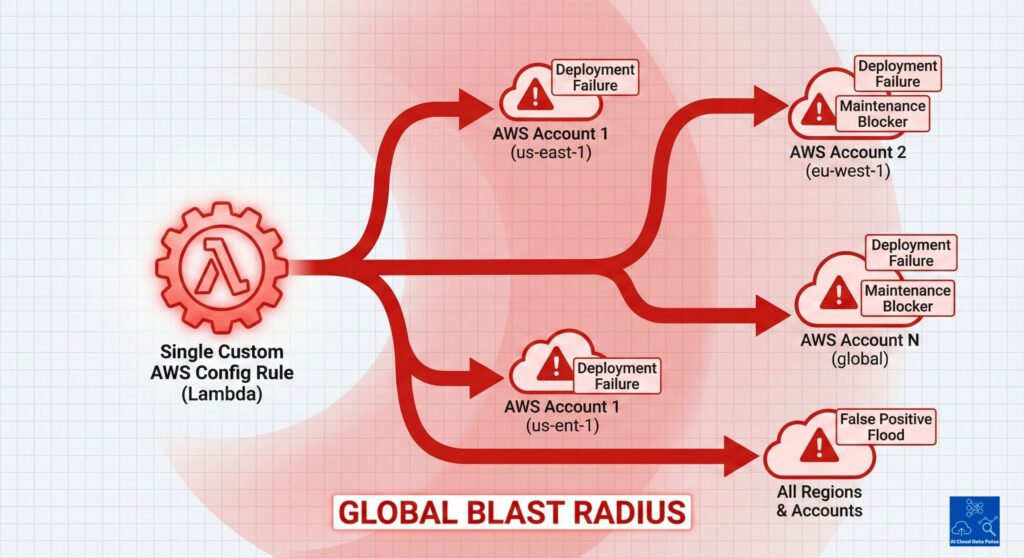
Because custom rules express governance policy at an organizational level, they are applied universally across multiple accounts and regions. They inherently become a critical point of failure that propagates across all these accounts and regions simultaneously. Furthermore, rule behavior change due to dependencies will affect all enrolled accounts simultaneously. Additionally, they are nominally hypersensitive, with false positives scaling far more quickly than real risk, flooding the monitoring with noise. Since there is a large footprint, this multiplies the investigation effort, burdening operational resources.
Ownership as a Security Control
Given the importance of maintaining and the impact of custom AWS Config rules, a key best practice is ownership. Therefore, governance should assign a clear owner who is accountable for rule behavior. Additionally, governance must ensure that intent is documented and preserved over time. Also, they should establish controls to ensure that custom rule ownership survives team and role changes, as they inevitably will. Otherwise, the consequence of unowned rules is that they will become untouchable risks.
Why Maintenance, Blast Radius, and Ownership Compound
The factors are interdependent, compounding issues with custom AWS Config rules, making best practices paramount. Whenever there is weak ownership, this will magnify the maintenance burden, adding costs to the organization. Concurrently, maintenance failures will amplify the blast radius as failures are distributed across all regions and accounts. Hence, these factors will contribute to signal degradation before visibility improves.
Signal Quality vs Rule Sprawl
The best practices for custom AWS Config rules are to achieve compliance visibility over the rule count, so meaningful information is present. Accordingly, they aim to prioritize high-fidelity signals instead of configuration drift signals becoming noisy. The central constraint is the limiting factor of human attention, and to prevent overwhelming human operators with too much information. Primarily, best practices should prevent noise from undermining security outcomes.
Having the ability to create custom AWS Config rules with low friction leads to quickly adding new rules, resulting in a rule sprawl. Additionally, incremental policy creep over time without pruning and review will also contribute to rule sprawl and configuration signals becoming noisy. Often, exceptions eventually get encoded as permanent controls that were intended to be temporary. This is accompanied by rare reviews or retirement of rules failing to halt the rule sprawl. This is further compounded by governance lagging behind rule growth.
Overwhelming human operators with configuration signals will invariably lead to alert fatigue and desensitization. This will result in them routinely ignoring critical findings or deferring action upon them. Conversely, they will also waste investigation effort on false positives, diverting attention from real alerts. This will significantly contribute to genuine misconfigurations being buried in the noise, resulting in significant resource configuration drift. More detrimental is the overall erosion of trust in compliance signals.
Best practices should aim for fewer, high-value compliance rules, ensuring that operators can effectively manage AWS environment configuration. They achieve this by prescribing clear intent for custom rules with accountable ownership. This is enhanced by conducting periodic signal review and pruning of rules and policies. Additionally, governance should favor restraint over coverage.
Conclusion: A Decision Checklist for Custom AWS Config Rules
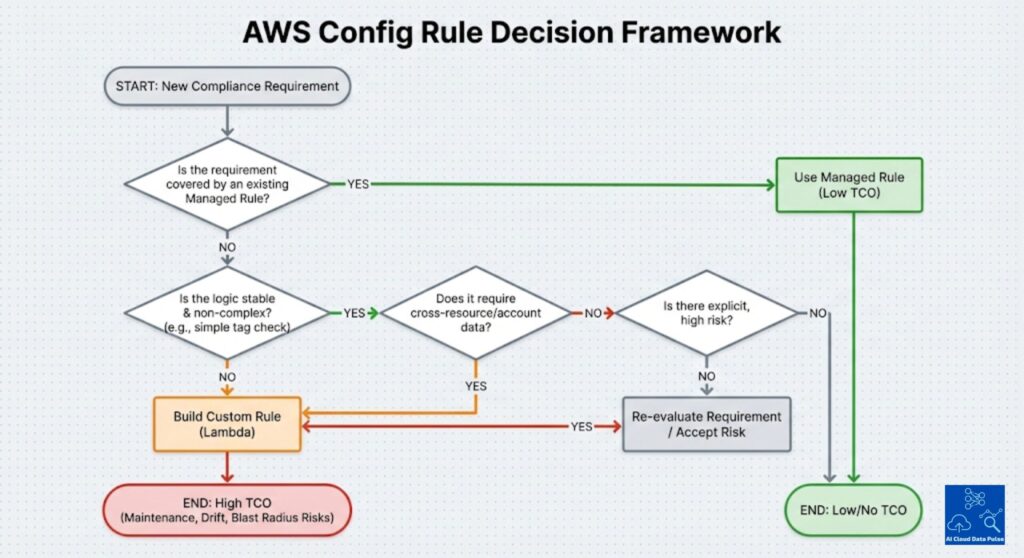
Custom AWS Config rules best practices necessitate the need for a decision checklist since often the same decisions are made across teams and time. Further, context and intent will decay over time, making many rules redundant and burdening operators. Also, checklists enforce consistency through explicit criteria. Additionally, checklists enforce shared standards, thereby strengthening governance.
For each proposed custom AWS Config rule, platform personnel should make the following decisions. The first is on whether existing AWS-managed rules are insufficient for organizational policies. They then should establish whether the compliance logic is stable and durable, minimizing decay over time. Additionally, they ensure clear ownership and maintenance for each rule. They also need to properly understand and accept the blast radius for each rule. Finally, they should prove that the signal value exceeds the operational cost.
Ultimately, best practices for custom AWS Config rules should treat them as production systems. Finally, this is an example of quality over quantity where security is strengthened through disciplined restraint.
Further Reading
Operational Best Practices for AWS Well-Architected Framework Security Pillar
Security Engineering: A Guide to Building Dependable Distributed Systems, 3rd Edition, by Ross Anderson
Site Reliability Engineering: How Google Runs Production Systems, by Jennifer Petoff, Betsy Beyer, Chris Jones, Niall Richard Murphy
Designing Data-Intensive Applications: The Big Ideas Behind Reliable, Scalable, and Maintainable Systems, Martin Kleppmann
Affiliate Disclosure: As an Amazon Associate, I earn from qualifying purchases. This means that if you click on one of the Amazon links and make a purchase, I may receive a small commission at no additional cost to you. This helps support the site and allows me to continue creating valuable content.