Best Practices: What Is AWS GuardDuty and Why It Matters
AWS GuardDuty Best Practices takes over from AWS Logging and Monitoring as the next logical stage in the security incident response workflow. It is an AWS-native threat detection service that continuously monitors the cloud environment for malicious or suspicious activity. Therefore, AWS GuardDuty provides threat detection based on the logging and monitoring output in the security response workflow.
How GuardDuty Detects Threats
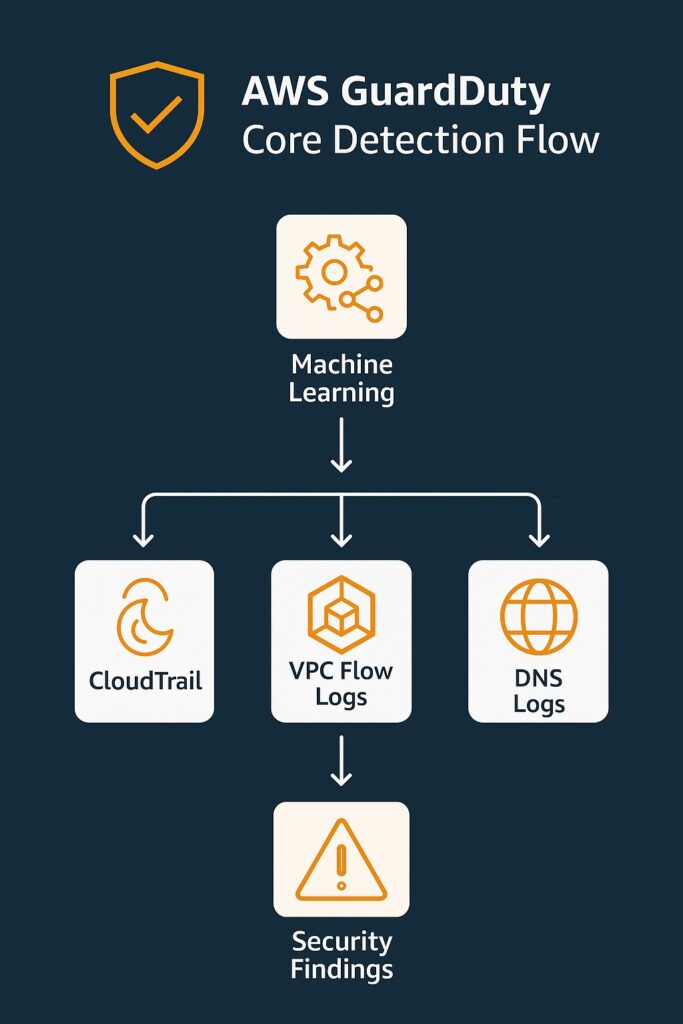
GuardDuty detects threats by employing machine learning models that identify anomalous behavior across AWS accounts and workloads. It also accesses AWS internal, AWS partner, and public intelligence sources for known malicious IPs, domains, and patterns.
Additionally, AWS GuardDuty performs sophisticated pattern analysis across CloudTrail, VPC Flow Logs, and DNS activity to detect malicious or abnormal behavior. Moreover, it performs runtime monitoring of the EKS surface area to detect container-level and Kubernetes-based threats. GuardDuty also continuously correlates all these events to surface high-severity security findings.
These activities clearly show that GuardDuty performs both anomaly-based and threat-intelligence-based threat detection. Moreover, these signals work together, not independently, to provide a comprehensive picture of the threat environment.
Key Data Sources GuardDuty Monitors
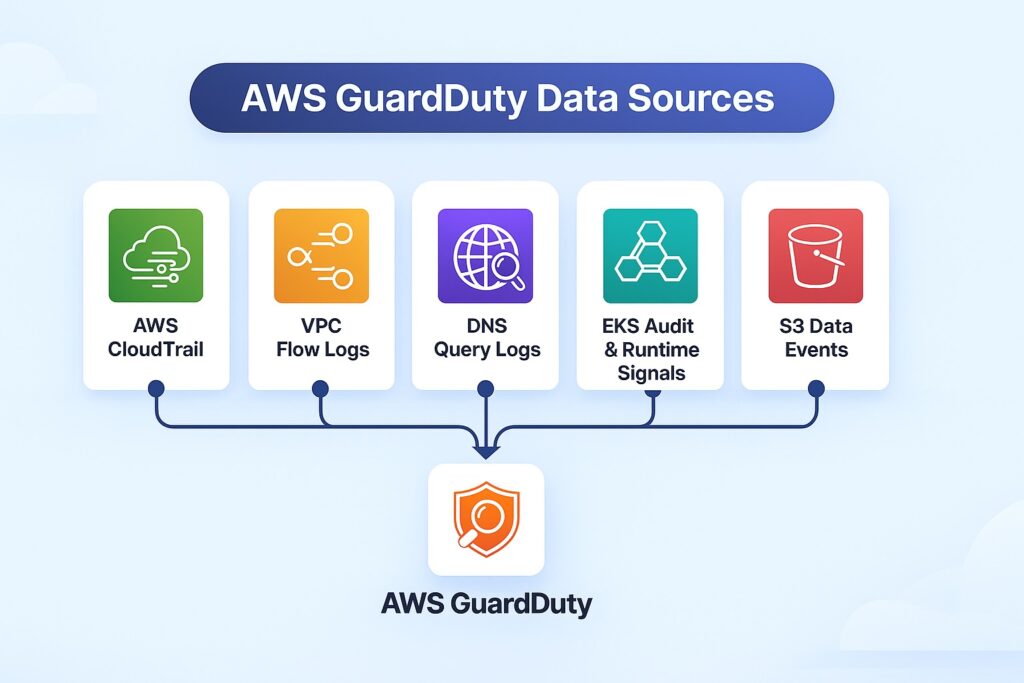
Several key data sources provide AWS GuardDuty vital information to effectively monitor the cloud environment, allowing the adoption of best practices. CloudTrail event logs, previously covered, capture API activity and account-level behaviour for detecting malicious behavior. Network traffic within VPCs is captured by VPC Flow Logs that reveal network traffic patterns and anomalies. DNS query logs are also a source for GuardDuty, as they enable it to identify outbound domain lookups and suspicious destinations. EKS audit and runtime signals are a significant source of information about the cloud environment since they expose Kubernetes workload and cluster activity. However, GuardDuty does not provide equivalent monitoring of ECS, despite it being a container-based service. GuardDuty also provides S3 protection by scanning S3 access logs to detect suspicious access patterns and anomalous or unauthorized data operations. One typical example that illustrates the necessity of S3 protection is attempts at data exfiltration.
Common Security Gaps Without AWS GuardDuty
GuardDuty is an essential part of any cloud sentinel that protects the AWS environment from active threats. Without it, malicious API activity and unauthorized account actions contained in CloudTrail logs will go undetected. Also, any security incident response will miss network anomalies indicating compromise or lateral movement that are within VPC Flow Logs. Moreover, any security solution will not have visibility into suspicious domain lookups or container behavior. Finally, without GuardDuty, correlation across these data sources is virtually nonexistent, with incident response running blind.
Not only is AWS GuardDuty essential, but equally important are best practices to ensure its effectiveness.
Best Practices to Set Up AWS GuardDuty the Right Way
GuardDuty, if not set up correctly, is less effective and makes the AWS cloud environment more vulnerable, hence the need for best practices.
Multi-Account Deployment with AWS Organizations
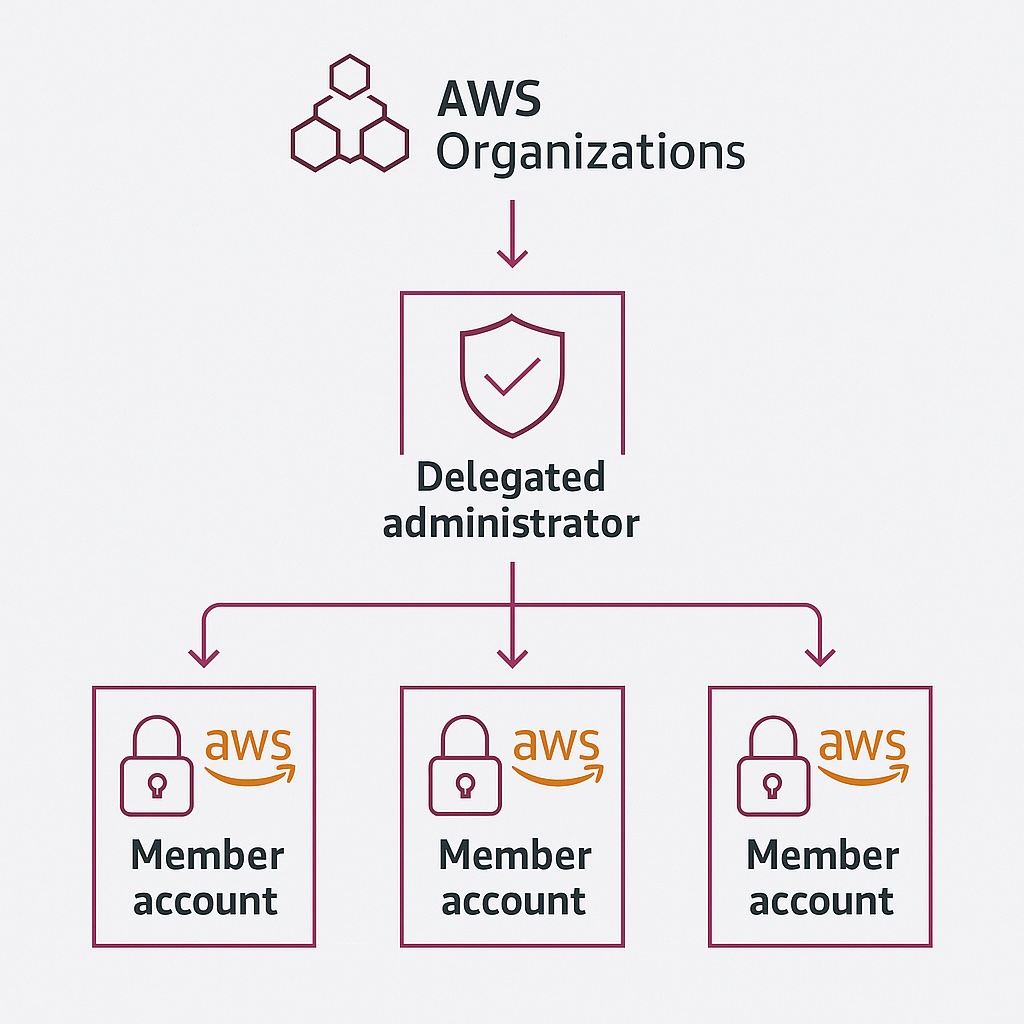
Most AWS organizational customers have multiple accounts, usually ranging from five to hundreds. Therefore, it is realistic to expect to secure environments consisting of many accounts and regions. Accordingly, it is sensible to centralize GuardDuty administration through a delegated administrator account. Likewise, establish automatic enrollment of new AWS accounts into GuardDuty for consistent protection.
Unified security visibility across all accounts is critical for securing the environment. Therefore, set up cross-account aggregation of findings. Another best practice is to implement organization-wide enforcement of AWS GuardDuty settings and data sources to ensure that certain accounts are not more vulnerable than others. Finally, manage GuardDuty at scale from a single location to reduce operational overhead.
Enabling All Supported Threat Detection Features
If some of GuardDuty’s threat detection features are not enabled, then it is less effective, and the AWS environment is more vulnerable. GuardDuty must provide complete coverage by activating VPC Flow Logs, DNS logs, and CloudTrail event integration. It must also provide container-level visibility, since most applications run in containers. Engineers achieve this by enabling EKS Audit and EKS Runtime Monitoring. Another way to extend protection is to turn on malware protection for EBS volumes and container images. Also, make sure that S3 Protection is enabled to detect suspicious access or data exfiltration attempts.
Integrating Malware Protection and EKS Runtime Monitoring
More specifically, EBS volumes and containers are a significant source of vulnerabilities and require greater attention to secure the environment. Therefore, deploy GuardDuty Malware Protection to scan EBS volumes and container workloads for malicious files. Also, it is crucial to capture kernel-level and process-level signals from Kubernetes workloads by enabling EKS Runtime Monitoring. A valuable benefit from leveraging both these features is that they detect threats that bypass network or API-level monitoring. This improves incident response accuracy by combining runtime indicators with GuardDuty findings.
Region Coverage and Why You Should Enable All Regions
This is an important AWS GuardDuty best practice since neglected regions are prime network locations for attackers to target. Therefore, it is vital that GuardDuty be configured to detect threats that may originate in unused or lightly monitored regions. This will prevent attackers from exploiting disabled regions that bypass GuardDuty visibility. Moreover, this will ensure consistency in organization-wide threat detection across all AWS workloads.
AWS GuardDuty Best Practices for Threat Detection
GuardDuty plays a critical role in securing the AWS environment, and following best practices further reduces vulnerabilities.
Enable All Available Data Sources
In addition to enabling all supported threat detection features, it is crucial to enable all available data sources for securing the environment. CloudTrail events are needed to provide API visibility and account-level anomaly detection. VPC Flow Logs are also required since they capture network patterns, traffic flows, and potential lateral movement. DNS query logs are another significant source of information, as they help identify suspicious domains, command-and-control traffic, and exfiltration attempts. Valuable information comes from EKS audit and runtime signals that monitor Kubernetes workloads and detect container-level threats.
Treat “High” Severity Findings as Immediate Action Items
To make GuardDuty truly effective, it is essential to act upon its alerts, especially its high-severity findings. These are displayed as indicators of active compromise requiring urgent investigation and containment. They also include potential unauthorized access or reconnaissance attempts targeting critical resources. Additionally, GuardDuty presents administrators with high-risk behavior suggesting credential misuse or privilege escalation. Also, findings that can quickly evolve into lateral movement or data exfiltration if not addressed.
Tune Suppression Rules Without Hiding Critical Events
Another aspect of GuardDuty findings is false positives and the signal-to-noise ratio. The challenge is to filter noisy or repetitive findings while preserving visibility into meaningful threats. Best practices aim to avoid suppressing GuardDuty’s high-severity or anomaly-based alerts that signal active compromise in AWS. This includes regularly reviewing suppression patterns to ensure they reflect current workloads and behaviors. Therefore, ensure operational efficiency without reducing GuardDuty’s overall detection coverage.
Configure Trusted IP Lists and Threat Intelligence Feeds
Intelligence feeds are another vital source of information contributing to GuardDuty’s effectiveness, along with trusted IP lists. Trusted internal IP ranges help to reduce false positives from known sources, achieving a greater signal-to-noise ratio. Integrating custom intelligence feeds into GuardDuty provides organization-specific Indicators of Compromise (IOC). Furthermore, enhancing GuardDuty findings with external threat data will increase its detection precision. Moreover, both the infrastructure and threat landscapes are continually evolving, necessitating regular updates to trusted IP and threat lists.
Leverage AWS GuardDuty’s MITRE ATT&CK Mapping
Adopt best practices from the cybersecurity industry by leveraging the MITRE ATT&CK framework implemented in AWS GuardDuty. Therefore, align GuardDuty findings to standardized adversary tactics and techniques. By understanding where each finding fits in the attack lifecycle, incident response becomes more effective. Additionally, having structured visibility across MITRE-defined behaviors will strengthen threat hunting.
Managing and Responding to AWS GuardDuty Findings
There is little value in configuring AWS GuardDuty to perform superbly but never acting on any of its findings. Therefore, effective incident response is also needed, as discussed previously. We will reiterate this discussion as applicable to GuardDuty as an information source.
Classifying Findings for Fast Triage
Some threats are more serious than others, or, as George Orwell will say, some threats are more equal than others. Therefore, best practices around AWS GuardDuty findings are to group alerts by severity to prioritize high-impact threats first. This is strengthened by identifying patterns across similar findings to streamline any investigation. Additionally, it is strongly recommended to separate benign or expected behavior from indicators of compromise to reduce response to false alarms. It is also recommended to tag findings by resource type for faster assignment to the right teams. Moreover, utilize historical context to distinguish new anomalies from recurring noise.
Automating Incident Response with EventBridge & Lambda
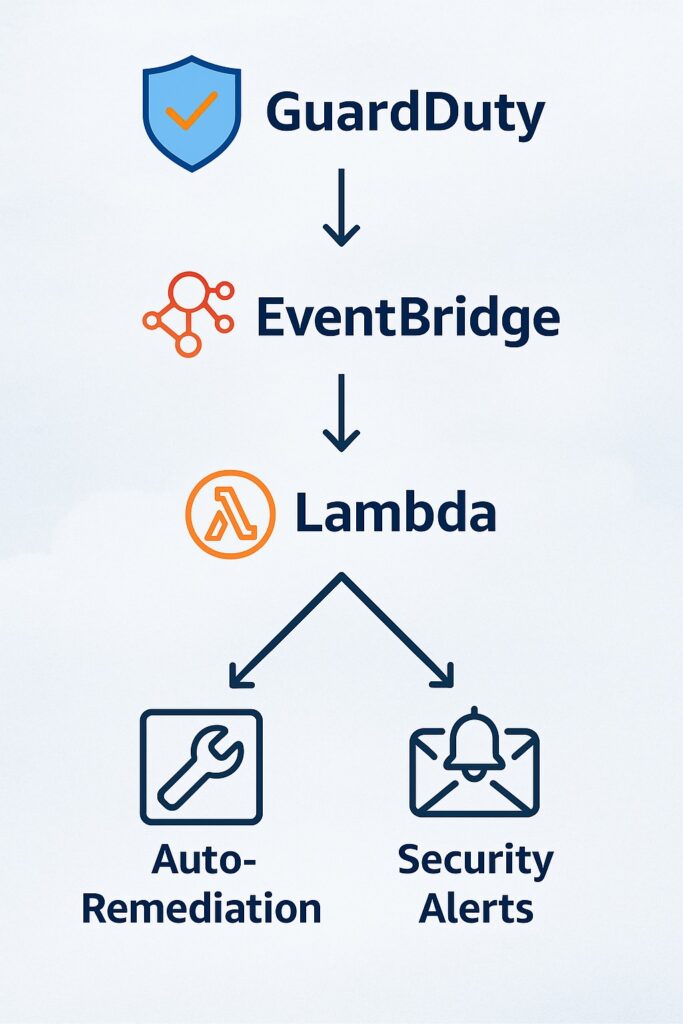
Also, in a previous article, automating responses to findings in AWS GuardDuty is a fundamental best practice. This is achieved when EventBridge rules trigger automated workflows based on GuardDuty findings. One category of automated workflows is Lambda functions that isolate compromised resources or revoke credentials. Another type of workflow is automating remediation actions, such as security group updates or IAM policy changes. Automated responses still require oversight, and therefore, they send real-time notifications to security teams via SNS or chat integrations. Another activity of automated operations is to enrich GuardDuty findings with additional context prior to taking action. Automated responses therefore reduce manual effort and response time by standardizing repeatable remediation playbooks.
Integrating AWS GuardDuty with Security Hub and Detective
It is true that no man is an island, and AWS GuardDuty is insufficient on its own for securing the AWS environment. Therefore, Security engineers must integrate GuardDuty with other security services. Many customers operate over multiple AWS accounts, and engineers should use Security Hub to centralize GuardDuty findings across all accounts. This provides the benefits of unified security visibility while correlating GuardDuty alerts with insights from other AWS security services. While GuardDuty performs threat detection, AWS Detective complements it by conducting investigations of suspicious activities with graph-based visualizations. Therefore, integration with Security Hub and Detective enables tracing relationships between resources, users, and unusual behaviors for deeper analysis. It also allows streamlined incident investigations by moving from alert to root cause within a single workflow.
Building a Repeatable Response Playbook
While it is important to automate responses to AWS GuardDuty findings, security engineers must ensure that the manual aspects are repeatable and consistent across all accounts. Therefore, they must define consistent, step-by-step procedures for handling common GuardDuty findings. By building a repeatable response playbook, they will standardize investigation and remediation actions to reduce response variance. This will ensure that teams can execute rapid, predictable workflows during security incidents.
Hardening Your AWS Environment with AWS GuardDuty Insights
It does not end with successfully responding to AWS GuardDuty findings, but using these findings to improve the overall security posture.
Reducing Attack Surface from Repeated GuardDuty Alerts
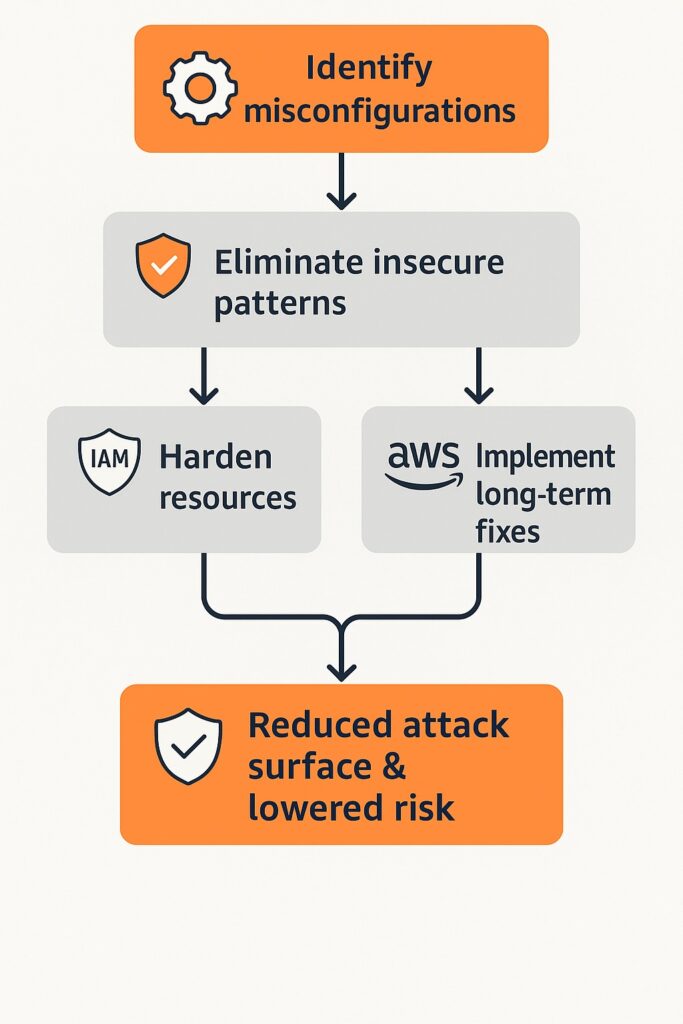
Recurring AWS GuardDuty findings often indicate deeper issues, necessitating engineers to identify recurring misconfigurations that expose resources to unnecessary risk. One important hardening activity is eliminating insecure patterns such as overly permissive IAM roles or open security groups. Another source of recurring GuardDuty findings is vulnerable resources that engineers should harden to prevent future findings. Additionally, engineers should think strategically and implement long-term architectural fixes rather than relying on temporary remediations to address GuardDuty findings.
Identifying Misconfigurations Leading to Findings
Another major source of GuardDuty findings is misconfigurations in the AWS environment. Best practices, therefore, recommend both manual and automated processes to review AWS GuardDuty alerts that point to insecure resource configurations. This includes spotting overly permissive access controls or exposed network paths. They should also highlight IAM policies, roles, or credentials that enable unintended access. Finally, they should trace findings back to configuration drift or overlooked security baselines.
Using Findings to Strengthen IAM and Network Policies
IAM and network policies are a significant source of AWS cloud vulnerabilities, resulting in a large set of GuardDuty findings. Therefore, both manual and automated processes should tighten IAM roles, policies, and permissions flagged as overly permissive or misused. This extends to refining security group rules and network ACLs to block suspicious traffic patterns. Additionally, processes should restrict access paths identified via GuardDuty findings as potential attack vectors. Another fundamental best practice is to enforce least-privilege principles based on repeated indicators of risky behavior from AWS GuardDuty findings.
AWS GuardDuty in a Multi-Account Enterprise Environment
We can never mention enough that most organizations operate across multiple accounts in an AWS environment. Therefore, AWS GuardDuty utilization must have operating across multiple accounts as its core design principle.
Centralizing Findings in a Security Account
Centralized management of the security landscape is paramount since each piece contributes to the overall security picture. Therefore, the security architecture should aggregate GuardDuty alerts from all member accounts into a single security account. This will enable unified monitoring and faster investigation by consolidating findings. Additionally, an integrated solution will reduce blind spots created by distributed or inconsistent account-level visibility. Therefore, the security solution should streamline incident response through a centralized, organization-wide security view.
Using Service-Linked Roles for Delegated Administration
While AWS GuardDuty centralization is of fundamental importance, this is complemented by GuardDuty operating across all accounts. Therefore, applying the principle of least privilege to AWS GuardDuty operating across these accounts is a core best practice. To ensure GuardDuty operates effectively, simplify cross-account management through built-in AWS service-linked permissions. This will reduce manual role creation and configuration errors in multi-account environments. Another key benefit is that it will ensure consistent enforcement of security settings across all organizational units. Additionally, it will enable delegated administrators to manage GuardDuty without full administrative privileges.
Implementing Least Privilege for Analysts and Responders
It can never be reiterated enough that the principle of least privilege is the foundational best practice for cybersecurity. Administrators must apply this throughout the AWS cloud environment, making this the most basic best practice supporting GuardDuty. Therefore, grant analysts only the permissions required to view and triage GuardDuty findings. Also, restrict responders to targeted remediation actions instead of broad administrative access. Engineers can achieve this by separating duties between investigation, remediation, and audit roles to reduce risk. Furthermore, by using IAM policies and permission boundaries, they will limit access to sensitive resources. Equally important is to review and adjust access levels regularly based on operational needs and GuardDuty insights.
Summary: AWS GuardDuty
GuardDuty is the backbone of any AWS cloud-based security solution that coordinates between logging, monitoring, and subsequent incident response.
Implementing AWS GuardDuty comes with a series of best practices to make it effective. First is multi-account setup since most organizations operate across multiple AWS accounts. Second, ensure full data source coverage since any missing data is a vulnerability ready for exploitation. Third, the absence of malware protection will cause considerable harm to the AWS environment. Lastly, is suppression tuning so dashboards are not noisy, making security ineffective.
Not only does GuardDuty detect threats from data sources, but there must be response systems to handle these threats. There are algorithms that actively triage these threats, so the focus is on the most serious threats. Also, engineers should make threat response automated, reducing manual workload and response time.
Engineers should integrate GuardDuty with Security Hub for an integrated and complete solution across the environment. Also, integrate it with AWS Detective, which performs investigations into the root causes of threats. Finally, implement playbooks as part of both manual and automated workflows for consistency and repeatability.
Further Reading
AWS Certified Security – Specialty (SCS-C02) Exam Guide by Adam Book and Stuart Scott
AWS: Security Best Practices on AWS by Albert Anthony
Practical Cloud Security by Chris Dotson
AWS Security by Dylan Shields
Security Chaos Engineering: Sustaining Resilience in Software and Systems by Kelly Shortridge and Aaron Rinehart
AWS Cookbook: Recipes for Success on AWS by John Culkin and Mike Zazon
Cloud Security Handbook: Effectively secure cloud environments using AWS, Azure, and GCP by Eyal Estrin
Affiliate Disclosure: As an Amazon Associate, I earn from qualifying purchases. This means that if you click on one of the Amazon links and make a purchase, I may receive a small commission at no additional cost to you. This helps support the site and allows me to continue creating valuable content.


