AWS Security Hub Findings: Introduction
AWS Security Hub findings address the issue of fragmented security signals from multiple independent AWS security signal services. Having disparate security signals makes it difficult to have a holistic view of the threat environment. Therefore, bringing them together into a consistent, structured format allows engineers and downstream automated security services to evaluate centrally. Also, security findings extend beyond detection and understanding to support visibility, prioritization, and monitoring.
Security Hub aggregates signals from multiple security services into a single place, enabling centralized security monitoring. These findings also provide severity, resource metadata, and workflow state that reflect both technical risk and operational context. Security teams and automated services are able to rapidly prioritize and triage emerging threats or concerns. However, security personnel must understand where findings come from and how they are used to realize Security Hub’s capabilities fully.
What are AWS Security Hub Findings Anyway
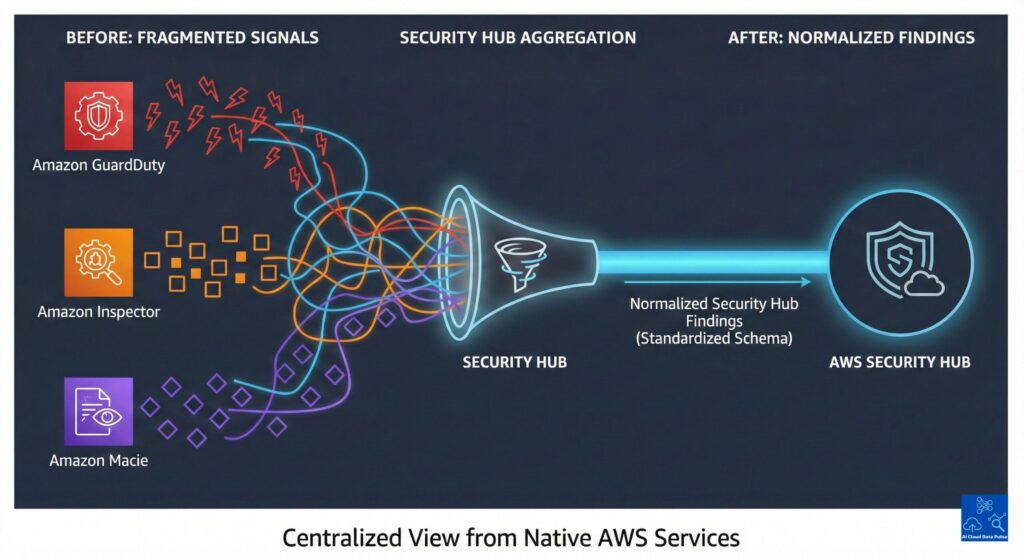
AWS Security Hub Findings as Normalized Security Signals
AWS provides several powerful services that generate signals in different formats, levels of detail, and structures. By normalizing these findings, AWS Security Hub preserves them and adds predictable fields such as severity, resource identifiers, and timestamps. It presents them in a standard format, having a shared structure for security teams and automated systems. They, in turn, can review, filter, and correlate security information from diverse sources in one place. Therefore, Security Hub prepares security telemetry signals and findings for downstream processing.
Where Findings Come From
AWS Security Hub primarily ingests signals and findings from native AWS security services, each specializing in threat detection, configuration assessment, and vulnerability analysis. Therefore, each source contributes a different type of security signal, some focusing on behavioral threats, while others focus on configuration drift or software vulnerabilities. Security Hub presents these different perspectives in a consistent format. Moreover, it provides centralized visibility without interfering with any of the source service’s operations. Significantly, its input services can be expanded to other third-party security tools and custom integrations, expanding visibility beyond native sources.
What a Finding Represents (and What It Doesn’t)
AWS Security Hub findings are the original security signals, with metadata that enhances understanding for more informed decision-making and action. However, they never replace logs, events, or raw detections, so they remain the authoritative source for investigation and forensic analysis. Security Hub findings primarily support visibility and prioritization and do not provide confirmed compromises or remediation decisions. This is the job of security personnel and downstream security services. For a broader view of how logs, metrics, and events support investigation and monitoring across AWS, see our guide to AWS logging and monitoring.
How AWS Security Hub Findings Are Generated
Detection at the Source
AWS Security Hub Findings are actually collations of findings from upstream security services, each focuses on a specific class of risk. It never performs detection itself but consumes security signals from the services that identify potential issues. Therefore, detection logic is defined and maintained by the originating services, preserving clear responsibility boundaries.
Multiple source services exist to focus on different classes of risk, some on behavioral threats while others assess configuration compliance or software vulnerabilities. Furthermore, these services operate independently of Security Hub and continue to operate even if Security Hub is disabled. Therefore, the findings of each of these services reflect their relative strengths and limitations, making it important to understand their origins when interpreting results.
Transformation into Security Hub Findings
AWS Security Hub’s real value lies in mapping findings to a common finding schema by aligning the data with a standardized finding format. Therefore, it normalized the findings data by ensuring that their fields, such as identifiers, timestamps, and categories, follow a predictable structure. However, it preserves the data’s original meaning. This is the crucial step for cross-service correlation by ensuring that they all follow a shared schema.
Aside from standard structure, AWS Security Hub also adds value by attaching additional metadata, including standardized attributes. These include severity labels, resource identifiers, and workflow states that enable easier tracking and prioritization of findings. However, Security Hub does not replace or modify the underlying findings, so the original source remains the source of truth. Therefore, the source service remains the owner and is responsible for the source data and not the Security Hub.
Continuous Updates and Lifecycle
Security Hub findings are continually updated by the source services whenever new data becomes available or conditions change, and they do not remain static. Therefore, the source services drive updates to existing findings due to changes such as resolution, recurrence, or escalation. Subsequently, the current state of findings reflects the current risk status that helps security teams or automated workflows track whether an issue is new, ongoing, or no longer relevant.
Therefore, Security Hub supports tracking findings over time instead of one-time alerting, allowing continual monitoring of issues and findings. Accompanying fields indicating workflow state or suppression status enable teams to control the handling of findings. When teams are aware of the findings lifecycle, this reduces fatigue by avoiding repeated reactions to the same issue.
Severity and Metadata in AWS Security Hub Findings
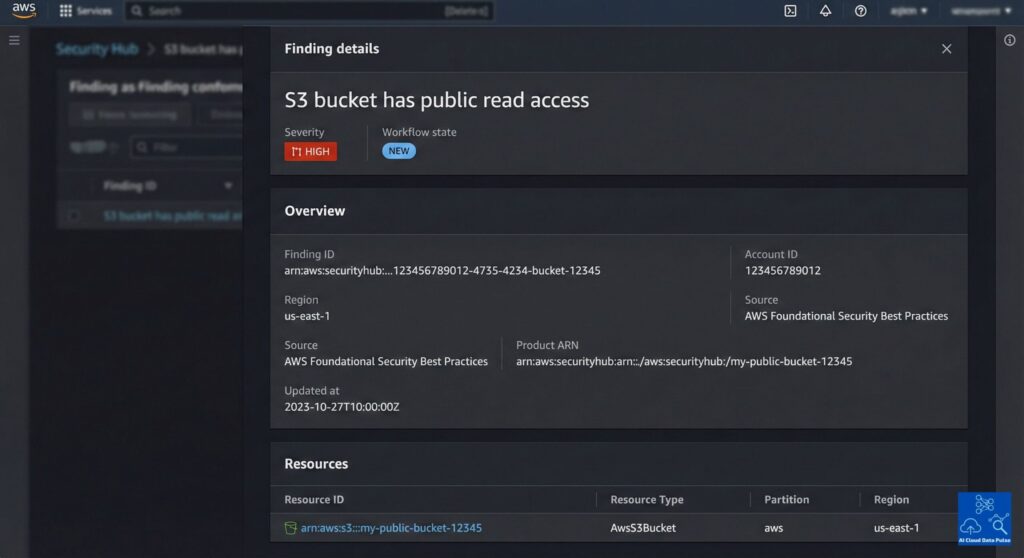
Severity as a Risk Indicator
AWS Security Hub findings severity expresses relative technical risk and not business impact since source signals are organization context agnostic. Significantly, Security Hub standardizes severity across different source services, allowing consistent comparison of findings from diverse signal sources. Severity reflects likelihood and potential impacts, and therefore is regarded as an area of attention and not as a confirmation.
It is important to understand that severity does not reflect business impact, but its seriousness from a technical perspective. Also, standardizing severity across different signal sources ensures its value is consistent for comparison, enabling prioritization and triaging. Severity indicates attention focus because it conveys an issue’s likelihood or potential impact, but is never a confirmation of an incident.
What Metadata GuardDuty Provides
AWS Security Hub adds value by enhancing source signal findings with metadata that identifies the affected resource and its environment. These contextual fields associate findings with specific assets and locations, preventing them from being abstract alerts. Additionally, time-based metadata assists teams in determining when an issue first appeared and whether it is recent, recurring, or historical.
Findings metadata is extremely useful when dealing with large volumes, as teams can apply filtering and grouping based on it. Also, metadata applies consistent contextual support to findings across diverse signal sources, therefore identifying findings that are related to the same resource or activity. Metadata allows teams to tune dashboards, alerts, and automation to focus on meaningful risk instead of raw volume.
Why Severity and Metadata Matter Together
AWS Security Hub provides both severity and metadata, since severity indicates that the finding needs attention, but provides no guidance on where to direct it. Therefore, metadata provides specific assets and conditions, allowing security teams to direct attention to the findings indicated by severity level.
These two finding attributes are implemented in workflows by grouping and visualizing findings in ways that reflect real environments. This also enhances automated response, where rules and workflows evaluate severity alongside metadata to determine which findings trigger an appropriate response. Furthermore, combining severity and metadata helps to reduce noise and prioritize operational risk.
Centralized Monitoring Usage in AWS Security Hub
Centralized Visibility Across Services
The key proposition of the Security Hub findings is a consolidated view of the threat environment across all AWS Accounts, regions. It presents a unified view of findings generated by different security services. This enables teams to understand the overall security posture and monitor potential issues without switching between service-specific consoles.
When teams have to switch between different security services, it fragments their monitoring workflow. Centralized review of findings reduces fragmented monitoring and simplifies teams’ monitoring activities. Additionally, this enables multiple teams to work better together, as they share a common view with consistent interpretation and prioritization.
Monitoring at Scale Using Filters and Views
Further value from centralized AWS Security Hub is that teams can apply high-level filtering and views consistently across findings from all security sources. These filtering and viewing capabilities can address information overload by allowing users to review subsets of findings that align with specific monitoring objectives. These include filtering on fields such as severity, resource type, account, and region.
Whereas individual sources focus on alerts, AWS Security Hub’s emphasis is on patterns across related findings supported by grouped views. This enables teams to identify recurring issues by grouping findings around shared attributes such as resource or account. Teams can monitor proactively by viewing trends and clusters of findings over time. This enables them to spot systemic risks and emerging threats before escalation.
For a practical example of how these patterns appear in real environments, see our deep dive on monitoring GuardDuty findings and common interpretation pitfalls.
Supporting Continuous Monitoring Workflows
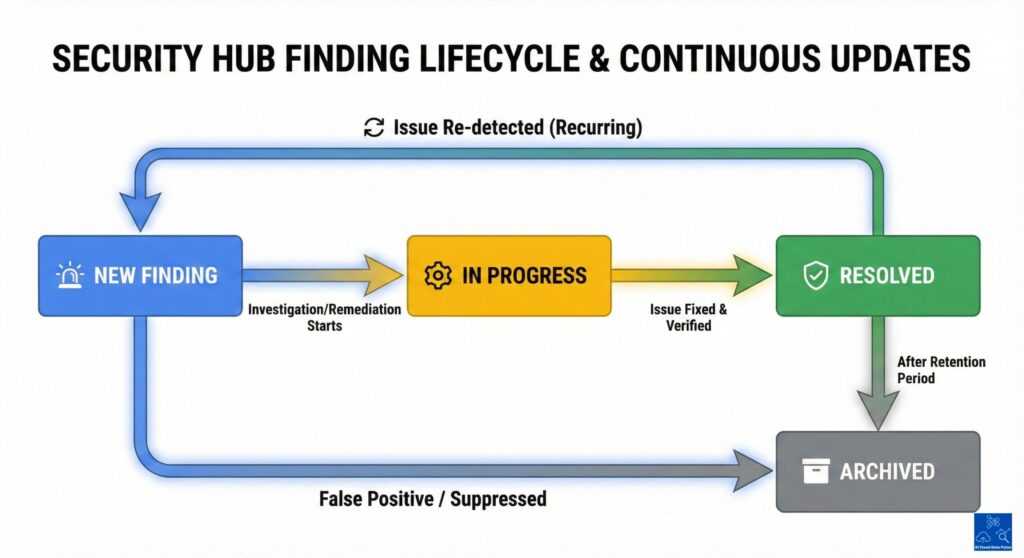
Additionally, centralized monitoring in AWS Security Hub enables teams to continuously monitor findings rather than only at fixed points or during incidents. This enables them to monitor findings as they evolve and helps them to distinguish between transient signals and risks. This reduces issues that remain unresolved across environments.
This continuous monitoring approach to monitoring further reduces reactive behavior. Hence, they avoid treating each new finding as an isolated event that they need to respond to immediately. This also reduces the need to repeatedly attend to unchanged or already-managed findings. Therefore, teams can prioritize meaningful changes in risk as part of their workflow.
Multi-Account Considerations for AWS Security Hub Findings
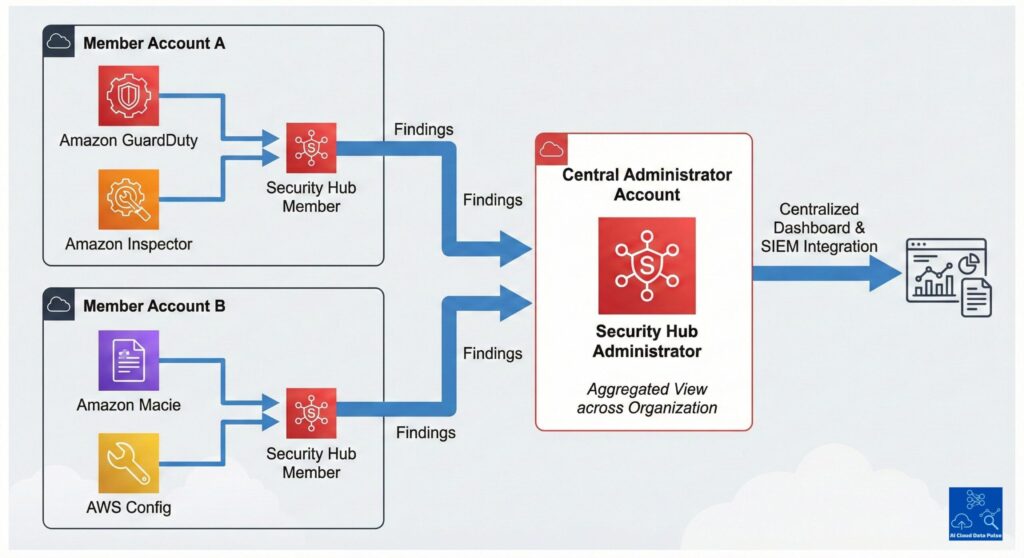
Centralized Visibility Across AWS Accounts
AWS Security Hub provides central visibility into findings across accounts, as mentioned above, allowing teams to monitor security posture across the organization. This improves teams’ ability to manage risk by assessing risk holistically rather than evaluating security findings in isolated account silos.
Significantly, these consolidated findings retain the originating account and region, ensuring full traceability in centralized views. Centralizing these findings never blurs ownership boundaries but provides clear attribution to owning accounts. Therefore, there is no loss of responsibility or accountability. The benefit is that context enables accurate triage across environments, having prioritization aligned with environment ownership.
Delegated Administration and Operational Impact
This is achieved through a central administrator account responsible for the central management of AWS Security Hub findings configuration and visibility. It also aggregates findings across member accounts while preserving organizational hierarchy without flattening account boundaries. This enables uniform monitoring practices across accounts, allowing teams to share interpretation of findings and severity.
Furthermore, consolidating findings into a central account simplifies monitoring workflows by providing a single point of visibility for organization-wide findings. It streamlines monitoring and review by reducing context switching between accounts. Meanwhile, it preserves account autonomy, enabling local teams to retain responsibility for remediation. Additionally, it reduces duplication, allowing faster triage through centralized views and routing of findings to responsible teams.
Common Misunderstandings About AWS Security Hub Findings
The core misconception around AWS Security Hub is that it performs threat detection; however, its role is to collate and organize findings from upstream services. Teams also mistake findings for raw logs; instead, they are summarized security signals with context. Neither do findings represent confirmed incidents, but are indicators of potential risk that require interpretation and validation.
Another mistake is assuming that severity represents business risk, whereas it is only a technical risk indicator. Organizational context is required for prioritization or triaging. Also, teams must remember that findings are tied to the originating accounts, and responsibility for remediation remains unchanged. Significantly, Security Hub is monitoring and not remediation, which is the responsibility of downstream services with human oversight.
Making Sense of AWS Security Hub Findings
AWS Security Hub findings are normalized security signals derived from multiple sources, designed for interpretation rather than direct action. Their role is to serve as inputs for human judgment and automated response systems. Therefore, their value emerges when severity and metadata are interpreted together, revealing patterns across services, accounts, and time. Overall, Security Hub complements rather than replaces detection and monitoring tooling by organizing and presenting security telemetry.
Further Reading
AWS Certified Security Study Guide: Specialty (SCS-C02) Exam by Alexandre M. S. P. Moraes
Practical Cloud Security: A Guide for Secure Design and Deployment by Chris Dotson
Affiliate Disclosure: As an Amazon Associate, I earn from qualifying purchases. This means that if you click on one of the Amazon links and make a purchase, I may receive a small commission at no additional cost to you. This helps support the site and allows me to continue creating valuable content.


